Let’s pick up right where Part 1 left off: pfSense Firewall Appliance Unboxing. This isn’t a quick-start guide. It’s my logbook from weeks of fine-tuning pfSense. Weeks, not years, so follow along and let’s learn and improve our pfSense configs together. In this article, I share my pfSense setup: interfaces, firewall rules, pfBlockerNG, Suricata, the… continue reading.
Let’s pick up right where Part 1 left off: pfSense Firewall Appliance Unboxing. This isn’t a quick-start guide. It’s my logbook from weeks of fine-tuning pfSense. Weeks, not years, so follow along and let’s learn and improve our pfSense configs together. In this article, I share my pfSense setup: interfaces, firewall rules, pfBlockerNG, Suricata, the… continue reading.
This article is a work in progress and will continue to receive ongoing updates and improvements. It’s essentially a collection of notes being assembled. I hope it’s useful to those interested in getting the most out of pfSense.
pfSense has been pure joy learning and configuring for the for past 2 months. It’s protecting all my Linux stuff, and FreeBSD is a close neighbor to Linux.
I plan on comparing OPNsense next. Stay tuned!
Update: June 13th 2025
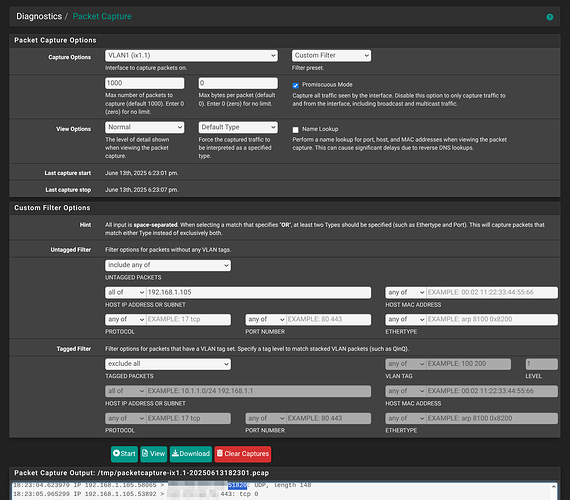
Diagnostics > Packet Capture
I kept running into a problem where the NordVPN app on my phone refused to connect whenever I was on VLAN 1, the main Wi-Fi SSID/network. Auto-connect spun forever, and a manual tap on Connect did the same.
Rather than guess which rule was guilty or missing, I turned to Diagnostics > Packet Capture in pfSense.
1 — Set up a focused capture
Set the following:
- Interface: VLAN 1’s parent (ix1.1 in my case)
- Host IP:
192.168.1.105(my iPhone’s IP address) - Click Start and immediately attempted to connect to NordVPN on my phone.
2 — Stop after 5-10 seconds
That short window is enough to grab the initial handshake. Hit Stop and view or download the capture.
3 — Spot the blocked flow
Opening the file in Wireshark or in this case just scrolling through the plain-text dump showed repeats like:
192.168.1.105 → xx.xx.xx.xx UDP 51820
192.168.1.105 → xxx.xxx.xxx.xxx UDP 51820
UDP 51820 is NordLynx/WireGuard’s default port. Every packet was leaving, none were returning. A clear sign the firewall was dropping them.
4 — Create an allow rule
On VLAN 1 I added one outbound pass rule:
![]()
Action: Pass
Protocol: UDP
Source: VLAN1
Destination port: 51820
The moment the rule went live, NordVPN connected instantly.
Packet Capture is often treated as a heavy-weight troubleshooting tool, but it’s perfect for quick wins like this: isolate one device, capture a short burst, and let the traffic itself tell you which port or host is being blocked.
Update: June 15th 2025
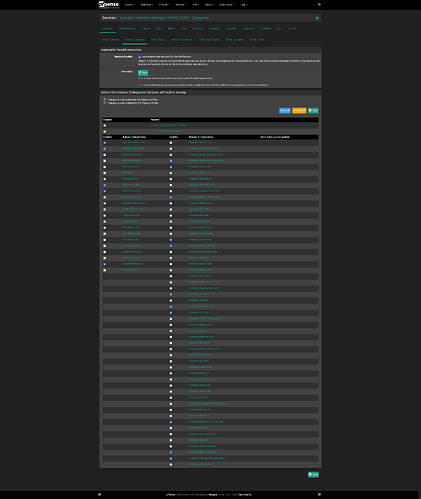
Keeping Suricata lean on a lightly-used secondary WAN
When you bind Suricata to a WAN that only has one or two forwarded ports, loading the full rule corpus is overkill. All unsolicited traffic is already dropped by pfSense’s default WAN policy (and pfBlockerNG also does a sweep at the IP layer), so Suricata’s job is simply to watch the flows you intentionally allow.
That means you enable only the categories that can realistically match those ports, and nothing else.
Here’s what that looks like on my backup interface (WAN2):
The ticked boxes in the screenshot boil down to two small groups:
- Core decoder / app-layer helpers –
app-layer-events,decoder-events,http-events,http2-events, andstream-events. These Suricata needs to parse HTTP/S traffic cleanly. - Targeted ET-Open intel –
emerging-botcc.portgrouped,emerging-botcc,emerging-current_events,
emerging-exploit,emerging-exploit_kit,emerging-info,emerging-ja3,
emerging-malware,emerging-misc,emerging-threatview_CS_c2,
emerging-web_server, andemerging-web_specific_apps.
Everything else—mail, VoIP, SCADA, games, shell-code heuristics, and the heavier protocol families, stays unchecked.
The result is a ruleset that compiles in seconds, uses a fraction of the RAM, and only fires when something interesting reaches the ports I’ve purposefully exposed (but restricted by alias list of IPs).
That’s this keeps the fail-over WAN monitoring useful without drowning in alerts or wasting CPU by overlapping with pfSense default blocks.
Update: June 18th 2025
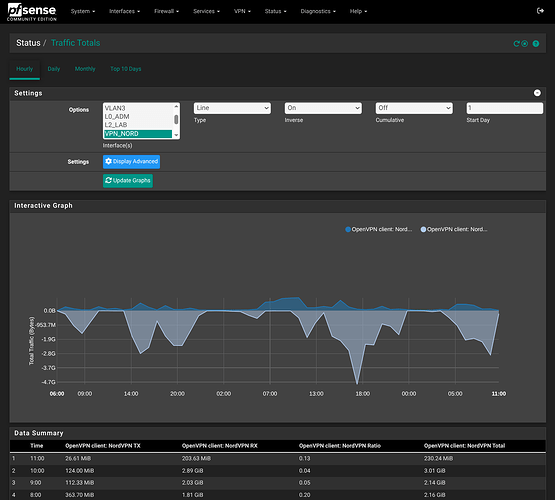
I added a new pfSense package called Status Traffic Totals:
Update: October 7th 2025
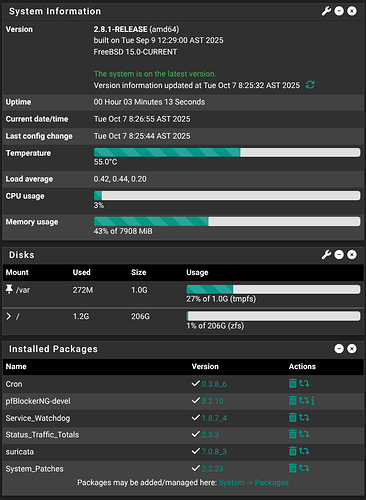
Upgraded to pfSense 2.8.1:
Fantastic article @hydn !
Over the years, the RFC 1918 (private addressing) egress configuration had me confused. I think part of the problem is that my ISP likes to send me a modem one year and a combo modem/router the next year…making this setting interesting.
I see that Netgate has finally published a good explanation and guidance for RFC 1918 egress filtering: