For the past three years, I’ve been putting off an upgrade to my network’s firewall. During that time, I was balancing multiple priorities: maintaining uptime with multiple ISPs, managing VPN performance limitations, and constantly watching the market for hardware that could check all the boxes without blowing the budget. I knew I needed better throughput,… continue reading.
For the past three years, I’ve been putting off an upgrade to my network’s firewall. During that time, I was balancing multiple priorities: maintaining uptime with multiple ISPs, managing VPN performance limitations, and constantly watching the market for hardware that could check all the boxes without blowing the budget. I knew I needed better throughput,… continue reading.
Some larger high-res photos (without lossy compression of the linuxblog.io):
This is Part 1, focused on the device I ultimately selected. Below, you’ll also find Part 1 and Part 2 of the decision-making process that led here:
Choosing the Perfect Network Firewall Device for under $300 — Part 1
My Quest for the Ultimate Home Office Firewall — Ok, well, Part 2
This is a cool little bit of hardware, but i cant help but feel like you overcomplcated the matter. A lenovo m720q (or similar) and a mellanox cx3 2x10gbe sfp+ card can be had for $1-200 and will get a bit more oomph.
Welcome to the community! ![]() thanks for taking the time to leave some feedback.
thanks for taking the time to leave some feedback.
Very possible! Living on an island in the Caribbean does complicate things a bit. Even if you gifted me a Lenovo Tiny (I actually have two), customs still assigns a value — gift or not — and charges duties based on their own assessment.
Returns aren’t practical either. Most used devices I buy when I’m in the U.S., so I can test and return them if needed. Shipping anything more than an envelope back from St. Kitts via FedEx starts at $100, so buying brand new to reduce risk often makes the most sense.
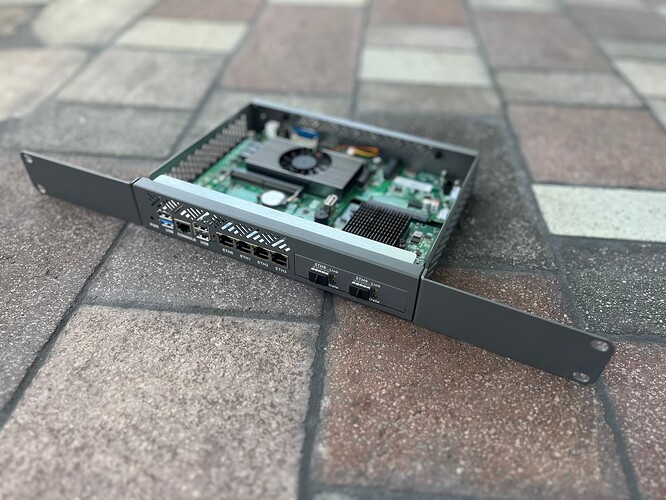
That said, I do take my time when deciding for analysis. Some of it’s location-driven, but some is just me being picky. I wasn’t interested in another Lenovo box this time. As mentioned in the article, I specifically wanted the extra ports + minimum x2 SFP. My current setup (pictured below) has 3 Ethernet lines running directly to 2 servers, my workstation, and the switch.
I wanted to keep close to that setup while routing the rest through the 1U switch:

The red cable is ISP1 and ISP2 is plugged in the back via USB WAN port:

With the new hardware appliance, I’ll be able to slide this in and plug everything up..
Oh, another example, is I recently gifted @shybry747 something. He also lives here. He called me and said something to the effect of: “what’s the best route to ship this here to reduce the cost on both me and him”. That said, I wouldn’t live anywhere else given the choice. Ha
Once again, thanks for adding the info and feel free to expand on the options because it will probably be helpful to the vast majority of readers.
Would go with opnsense over pfsense. Got a similar box as well (n100 4*2.5gbs) purchased directly from AliExpress. The most ironic part is the firewall is Free BSD based posted in a Linux community.
Hi @Dpwcnd welcome to our Linux community. ![]()
TBH, between the two, I was originally leaning toward OPNsense.
I went with pfSense mainly for performance and patch speed. WireGuard, for example, is significantly faster on pfSense (sometimes 2x faster) due to better integration.
pfSense also tends to patch critical security updates faster. OPNsense is often days but sometimes weeks slower than pfSense and still lags behind on certain features.
As for FreeBSD on our Linux & Technology forums, it’s not really about OS tribalism. Generally, if something solves a tech problem, it’s welcome.
Edit:
The FW appliance is for a home lab, so pfSense won’t be the only solution I test. This is a chance for me to explore, learn, and compare pfSense as well as OPNsense but also:
IPFire — Linux-based. Strong support for IDS/IPS, VPNs, and QoS. Good web UI.
Sophos XG Home Edition — Feature-rich firewall with a modern UI. Excellent UTM (Unified Threat Management) features. Free for home use with restrictions to features.
NG Firewall — Slick web GUI, very user-friendly. Strong content filtering, app control, and VPN. A free version available, but many features require a paid license.
VyOS — Enterprise-grade and CLI-based (Debian under the hood). Rolling release with strong routing features and VPN. I’m too noob to jump into this before pf/OPNSense.
However, I want to start with pfSense first and see how that goes.
Can you link to where you purchased the hardware please?
HI @Brad see link:
Or via Amazon listing for easy returns if you are in the US.
Hopefully, once I test this, I can actually report something positive. I was already asked by someone who tried a similar spec box:
How are the i226-v going? I have the same NICs in a miniPC i got and because the manufacturer hasn’t updated the NVM for the NICs they drop out continuously in PFsense. Made it useless for PFSense use.
Not the same device, so my fingers are crossed because I can’t return it. ![]()
Also, note that a 5% discount off all items on xxipc.com (firewalls, mini PC, etc. etc.) has been added to all supporter tiers.
Edit:
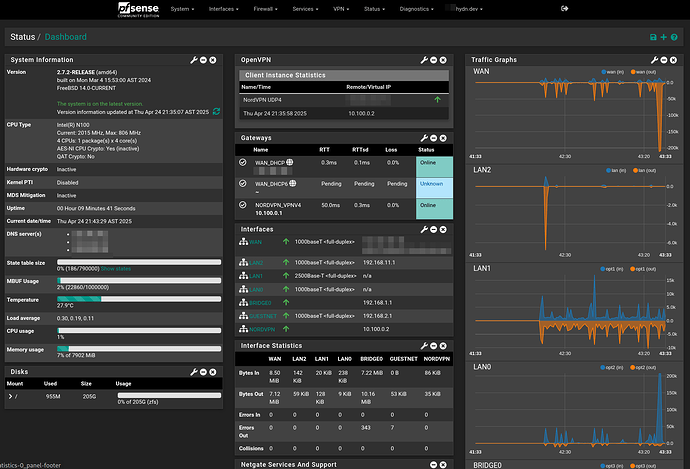
Starting setting up (mostly learning) pfsense today. The device itself is exceptional. The CPU is still near idle @300Mbps using OpenVPN. Eventually, will switch that to NordLynx (even more efficient) but the setup is a bit more times-taking. The 2.5G posts all work well. I’m still waiting on the SFP+ modules and of course the switch. So, like I said, mostly learning. I have restored to factory settings 3 times today already. ![]()
Will be sure to include testing results in part 2.
Edit: a few hours later…
off to bed!
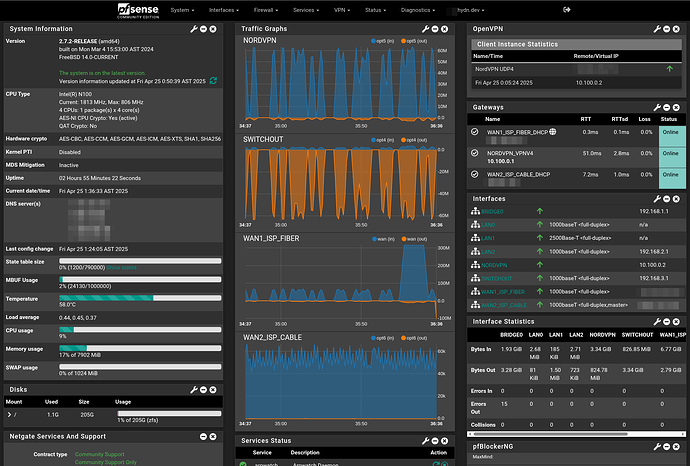
I’ve been setting up pfSense. It’s been an amazing experience thus far. I’m about 90% there. I have a TON to share! Soon, need up to another week or two with it.
It feels a lot like the days when I first started using Arch, in that, you really get to customize your security stature exactly the way you need and tailor it to fit your network. I have both IDS and soon IPS setup, just the final touches. Have been monitoring and cleaning up alerting/noise.
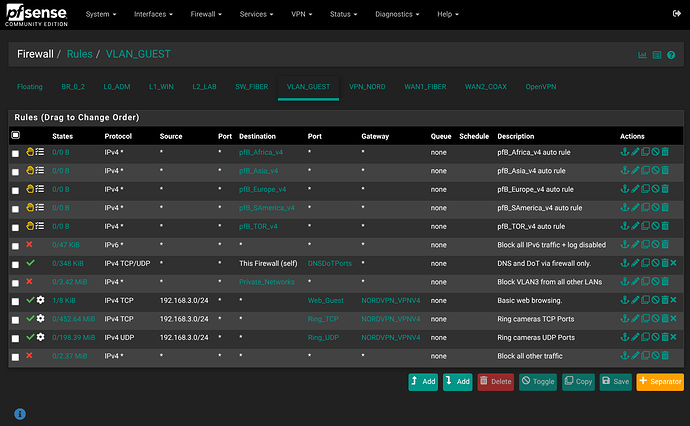
Have started the process of securing guest Wi-Fi. Inbound but also restriction to outbound in the rare even someone connects with a compromised advice.
Will follow up with more in Part 2 soon, continuing to learn, change and improve config!
Edit:
Part 2 is up:
Epic fail on my part with deleting the ISP ONT and using the GPON stick. The stick I purchased Sercomm FGS202 isn’t compatible with Intel 82599ES SFP+ NIC which can only connect at 1G or 10G.
So I wasted $45. Plus, shipping and import duty. ![]()
I wanted to delete BOTH ISP devices, the router AND the ONT modem. But for now, 1 will have to be enough. It’s a waste of electricity having the ONT plugged in when the pfSense appliance is more than capable of connecting via fiber. But for now I’ll leave things as is.
Hi, I like your writing, taste and style. I might get the same hardware your using and follow along as a good learning opportunity, plus I’ve been wanting to do all this myself for about 3 years too.
My question was, what is your preferred VPN host that you use with WireGuard? Also, I see a Celeron is the processor in this box, is there anything you’d reccomend to me now that’s more cost effective? I dont think I have a use for the SFT ports, I need to keep reading and find out why you wanted them.
Hi @rogerash0
Thanks for the feedback! Welcome to our Linux forums ![]()
No regrets on this firewall hardware. It runs great. My home office runs without the AC on 95% of the time, and the temps of the N100 is very ![]()
If running in an AC-cooled room, I would 100% recommend unplugging and removing the fan, it’s pointless. Quiet, but a complete waste, as the N100 is very cool-running CPU.
I prefer NordVPN, I’ve been using OpenVPN because NordVPN does not support WireGuard, only their NordLynx. However, I’m getting full ~480 to 500 Mbps symmetric speeds using OpenVPN, so I really don’t see any need to switch. Just be sure to enable
AES-NI CPU-based Acceleration for OpenVPN (best performance):
You can see my config details and settings here:
I still recommend the N100 because of its performance-to-heat ratio.
For my setup, cooling is important. I have not played with many firewall CPUs, so that’s really the only CPU I can recommend. I used this website to assist in my research: