I updated my Kali Linux install this morning and saw this change. (above screenshot)
This update showcases why I like being on Kali Linux or on Debian* in general; while Kali is based on Debian Testing, sometimes Kali will include packages from Unstable to get the latest features and security updates, especially for the cybersecurity tools.
This practice allows Kali to maintain its cutting-edge nature while still benefiting from the stability of Debian Testing.
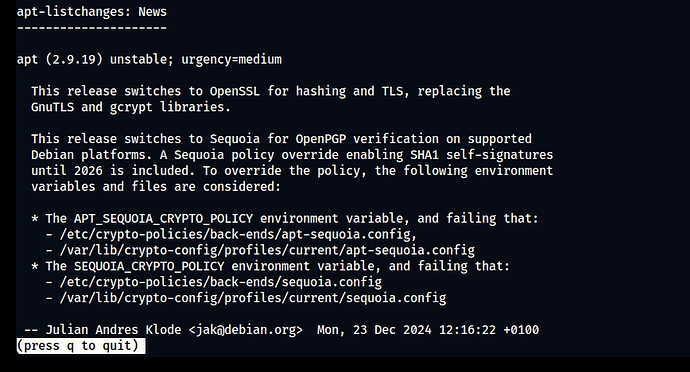
Debian users who keep their systems up to date will eventually notice this new apt 2.9.19 release. This update to the unstable branch brings two changes: OpenSSL for hashing and TLS, and Sequoia for OpenPGP verification. Let’s look at these changes and what they mean.
OpenSSL for Hashing and TLS
apt used to use GnuTLS and gcrypt for crypto operations. In 2.9.19 Debian developers switched to OpenSSL for hashing and TLS. Here’s why that’s interesting:
- Performance: OpenSSL is known for its optimized performance for cryptographic needs.
- Unified Library Usage: Many Debian packages already depend on OpenSSL, making it more efficient to standardize cryptographic operations across the ecosystem.
For end-users, this change should be seamless. But if you had configuration or scripts that used GnuTLS or gcrypt in some way, you might want to double-check for compatibility.
Sequoia for OpenPGP Verification
The other change in this update is the switch to Sequoia for OpenPGP verification. Sequoia is a modern OpenPGP implementation, designed to be secure, modular and easier to integrate than old solutions like GnuPG. With this update, apt now uses Sequoia to verify signed packages.
- SHA1 Self-Signatures: By default this update allows SHA1 self-signatures until 2026. This provides some backwards compatibility for legacy packages that still use SHA1 but you should really migrate to stronger algorithms if you can.
- Policy Overrides: Advanced users or administrators can override the default cryptographic policy by setting environment variables or editing configuration files. The following options are available:
- Environment Variables:
- APT_SEQUOIA_CRYPTO_POLICY: policy for apt.
- SEQUOIA_CRYPTO_POLICY: policy for Sequoia.
- Configuration Files:
- /etc/crypto-policies/back-ends/apt-sequoia.config
- /var/lib/crypto-config/current/apt-sequoia.config
- /etc/crypto-policies/back-ends/sequoia.config
- /var/lib/crypto-config/current/sequoia.config
You can customize these by editing the files or setting the variables in your environment. This allows you to have stricter or more relaxed crypto policies according to your needs.
Key Takeaways
- OpenSSL Adoption:
- Faster and aligned with the rest of the Debian’s cryptographic ecosystem.
- No required changes unless you have specific dependencies on GnuTLS or gcrypt.
- Sequoia Integration:
- A more modern OpenPGP verification.
- Default support for SHA1 self-signatures until 2026 for legacy packages.
- Easily configurable cryptographic policies for advanced users.
- What’s this mean for you:
- Regular users: no changes needed (seamless).
- Administrators and developers: review your config and update your policies if needed.
Conclusion
These changes are currently Debian specific. This is part of the Debian experimental 2.9.x branch, which will be used for the upcoming APT 3.0.
While this is Debian specific for now, other distributions (like Ubuntu) might adopt similar changes in the future. I’m speculating a bit, but seems likely.
So if you are using Debian Unstable (or derivatives pulling from it), you will see this with apt 2.9.19. Others will stay with their current version for now.
Reference:
Note the date in the screenshot, I don’t use my laptop as often, so I usually apply updates every few weeks. Which is why I’m only seeing this today.
Edit: Well this…Debian Package Tracker